SpringSecurity+JWT实现的登录认证
1、简介
Spring Security
在 Web 编程开发中,登录安全往往也是很重要的一个部分,而 Spring Security 所做得就是这个工作。在 java 领域,成熟的安全框架解决方案一般有 Apache Shiro、Spring Security 等两种技术选型。Apache Shiro 简单易用也算是一大优势,但其功能还是远不如 Spring Security 强大。后者可以为应用提供声明式的安全访问限制,他提供了一系列的可以由开发者主动配置的 bean ,并利用 Spring IoC和 AOP等功能特性来为应用系统提供声明式的安全访问控制功能,减少了诸多重复工作。JWT
JWT 的全称是:Json Web Token 。是在网路应用中传递信息的一种基于 json 的开发标准,可用于作为 json 对象在不同系统之间进行安全地信息传输。主要使用场景一般是用来在身份提供者和服务提供者间传递被认证的用户身份信息。
2、设计登录认证所用的表
本次登录认证需要用到三个表,分别是用户表,身份表以及用户和身份绑定的表。``
1 | SET NAMES utf8mb4; |

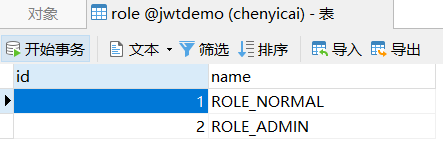
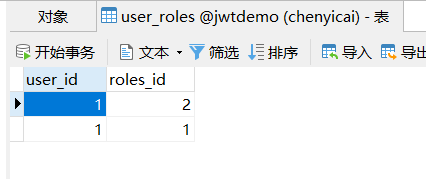
3、创建新工程并导入依赖及实体类
在创建一个SpringBoot工程之后我们需要引入Security和JWT必须的依赖
1
2
3
4
5
6
7
8
9
10<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt</artifactId>
<version>0.9.0</version>
</dependency>在配置文件中配置数据库信息
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24spring:
datasource:
driver-class-name: com.mysql.cj.jdbc.Driver
url: jdbc:mysql://localhost:3306/jwtdemo?useSSL=false&serverTimezone=UTC&allowPublicKeyRetrieval=true
username: chenyicai
password: cyc1234
ackson:
serialization:
indent_output: true
server:
port: 8086
#日志级别(一般设置为INFO)
logging:
level:
cn:
edu:
guet:
mapper: debug
org:
springframework:
security: info
mybatis:
type-aliases-package: cn.edu.guet.entity
mapper-locations: classpath:mapper/*.xml创建用户以及身份实体类
Users类:(省略 getset 方法)
此处所创建的 User 类继承了 Spring Security 的 UserDetails 接口,从而成为了一个符合 Security 安全的用户,即通过继承 UserDetails,即可实现 Security 中相关的安全功能。
1 | public class User implements UserDetails { |
Role类:(省略 getset 方法)
1 | public class Role { |
4、JWT工具类
该工具类主要用于对 JWT Token 进行各项操作,比如生成Token、验证Token、刷新Token 等
1 |
|
这里还有一个常量类,存储了JWT的一些常量信息
1 | public class Const { |
5、Token过滤器
用于每次外部对接口请求时的Token处理
1 | public class JwtFilter extends OncePerRequestFilter { |
6、Service层业务操作
主要是登录以及注册的业务
首先是AuthService接口:
1 | public interface AuthService { |
AuthServiceImpl实现类:
1 |
|
然后是 UserService 实现类,它实现了 UserDetailsService,可用于在登录认证时检验用户的身份
1 |
|
7、Spring Security配置类编写
这是比较重要的一点,这里决定了拦截的页面以及其他的一些操作。这是一个高度综合的配置类,主要是通过重写 WebSecurityConfigurerAdapter 的部分 configure 配置,来实现用户自定义的部分。
1 |
|
8、接下来编写Controller类进行测试
首先是登陆注册的类:
1 |
|
然后是测试权限的类:
1 |
|
9、现在我们进行测试
首先测试能否正常登录并获取到Token
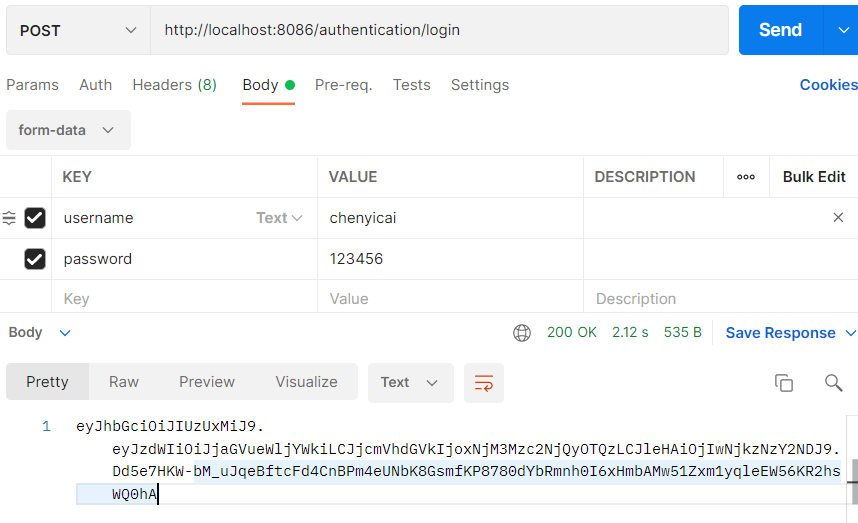
可以看到在账号密码正确的情况下,能返回一个Token,接下来只要访问网页时带上这个Token,就可以顺利进行访问接下来测试能否正常访问网页
首先是不带Token的情况: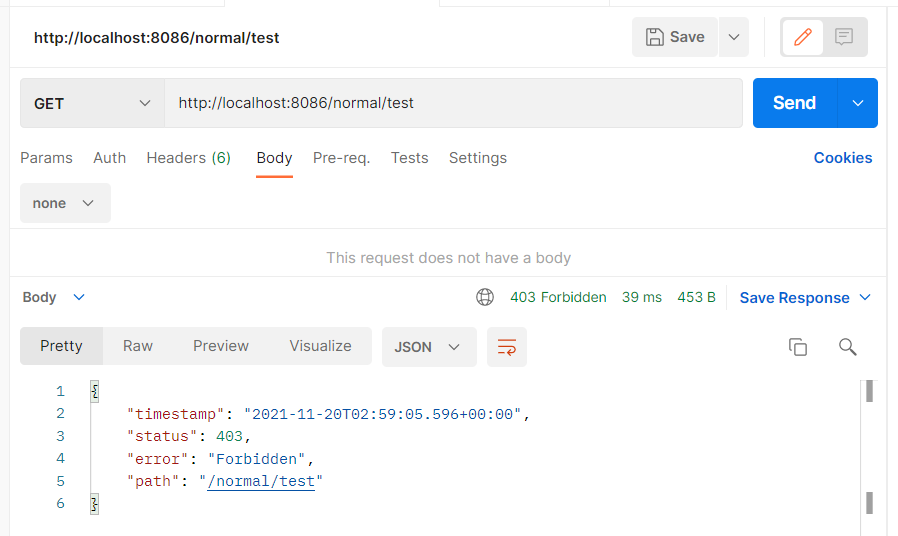
很明显,被拒绝访问了。
接下来我们测试一下携带Token的情况: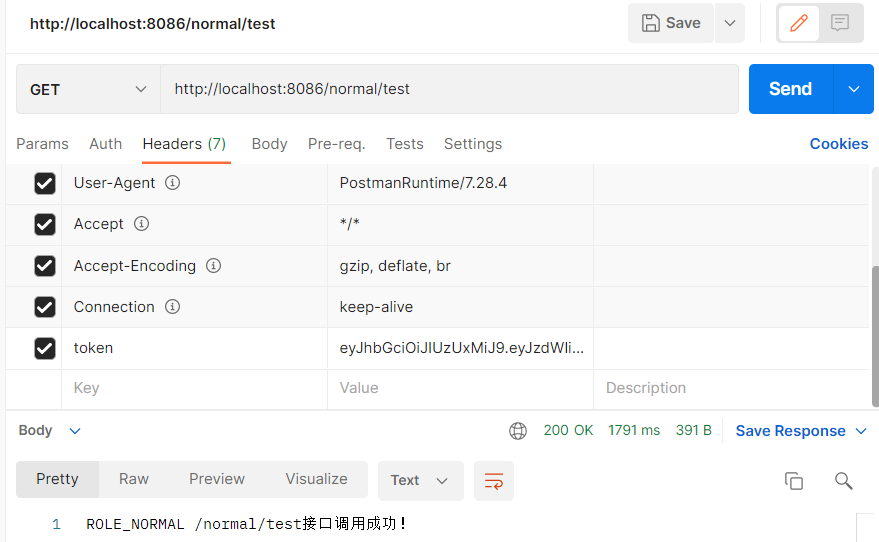
可以成功访问。










